VAPT
In today’s digital landscape, web security is a top concern for any organization with an online presence. Cyber threats are constantly evolving, and it’s essential to fortify your website against potential vulnerabilities. One aspect of web security that often goes overlooked is the proper configuration of security headers.
Security Headers in Espire XM Cloud Plus
1. X-XSS-Protection: Enabling the XSS Protection HTTP Response Header in the web application will prevent attackers from carrying out common reflected cross-site scripting attacks. X-XSS-Protection should be configured with “1; mode=block”
2. X-Content-Type-Options: The X-Content-Type-Options HTTP header prevents content sniffing, ensuring that MIME types specified in the content types headers are not changed by the server. This helps block content-type sniffing attacks. Use X-Content-Type-Options: nosniff.
3. HTTP Strict Transport Security (HSTS): The HTTP Strict-Transport-Security response header (often abbreviated as HSTS) informs browsers that the site should only be accessed using HTTPS, and that any future attempts to access it using HTTP should automatically be converted to HTTPS.
4. Content-Security-Policy (CSP): CSP is a critical security header. However, the example CSP policy provided in Sitecore’s default configuration might need adjustments. It’s crucial to create a strong policy tailored to your website’s specific needs. CSP is an added layer of security that helps to detect and mitigate certain types of attacks, including cross-site scripting (XSS) and data injection attacks. To enable CSP, you need to configure your web server to return the Content-Security-Policy HTTP header.
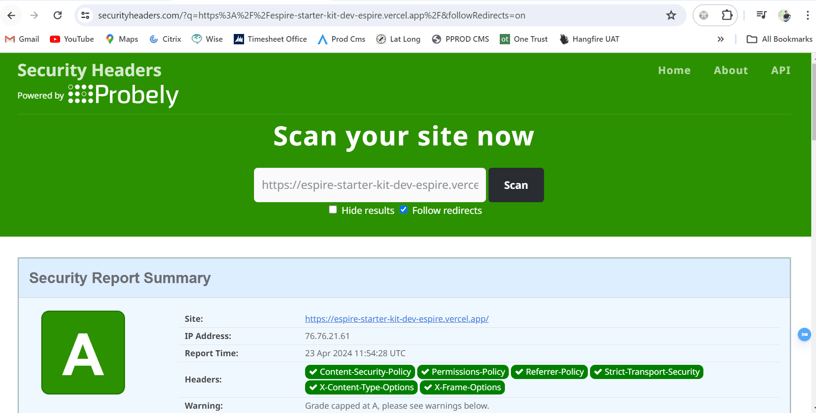
Website built using our stater kit receive an ‘A’ score on https://securityheaders.com/
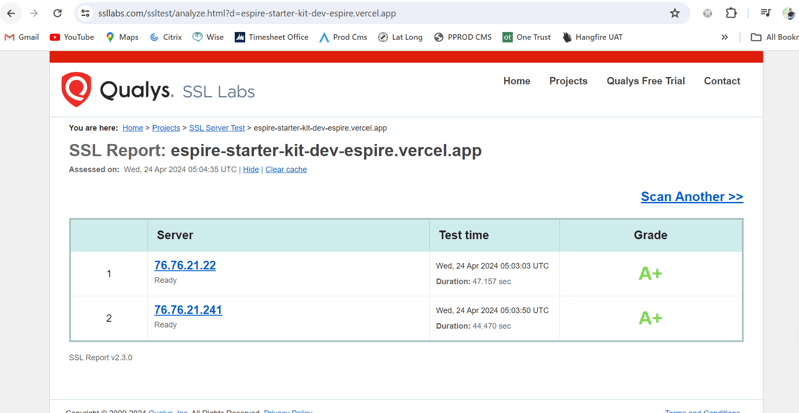
A+ Score on https://www.ssllabs.com/ssltest/